10 Ways to Protect Your Organization Now
Organizations depend on third-party commercial software not only for securing their networks, but also for managing and storing customer data, financial accounting and reporting, and fulfillment of core business processes. Managing the cyber aspects of these software supply chains is an area of critical concern.
What is a Software Supply Chain Attack?
A software supply chain attack involves the infiltration of software developer systems and data. The attacker is able to insert malicious code into a software component that is then compiled into a released software package. The compromised package is then made available to customers of the software provider as an update to the package they are currently using.
The steps used in the SolarWinds attack were highly sophisticated ...
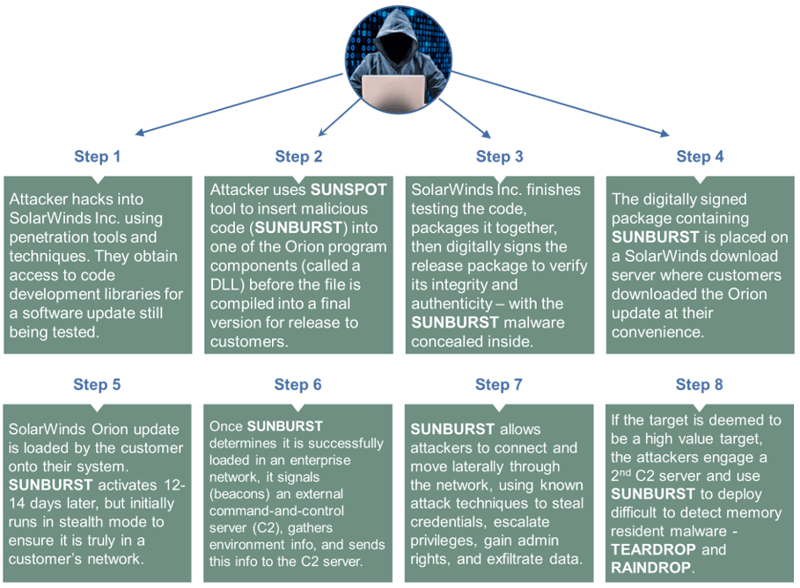
What Makes this Attack so Difficult to Detect?
Attackers using this technique were highly sophisticated and took special care to avoid detection. Their attack spanned multiple months as they carefully assessed the target environment, and evaluated how best to insert their malicious code that became a backdoor for later attacks.
Steps these threat actors used to hide their activities included:
- Using naming conventions that aligned with those used by the target company
- Using files names that resembled legitimate Windows files and directories
- Using advanced encryption to make it more difficult to detect the attack
- Turning off event logging during major hacking activities
- Altering network configuration settings to avoid triggering alarms
What is the Potential Business Impact on Customers?
The impact on the customers who unknowingly loaded the malware is difficult to calculate, but could potentially include:
- Stolen intellectual property
- Stolen customer data
- Disclosure/ransoming of highly sensitive information
- Compromise of key financial systems and unauthorized movement of funds
- Investigative costs to ascertain the scope of the breach
- Costs required to sanitize the IT environment and remove any backdoors
- Impact of public disclosure on stock value and market share
- Cost of lawsuits and potential regulatory actions
- Price increases for cyber insurance or cancellation of policy
What are steps that organizations need to take now?
As we can see, individuals with malicious intent are taking advantage of current weaknesses in the software supply chain to launch attacks and break down defenses. Keeping this in mind, I have identified 10 steps your organization should be taking right now. In Part 1, I provided you with the first 5 steps. Here are steps 6 through 10:
- Incident Response Capability – No matter how sophisticated an organization's defenses are, a breach will inevitably occur. How the organization responds to that breach can make all the difference between limited impact and massive outage. Having an Incident Response Capability in place is critical to being able to effectively respond to an attack. The incident response process has four major phases (Preparation, Detection & Analysis, Containment Eradication & Recovery, and Post-Incident Recovery). Careful attention should be given to establishing formal plans and procedures for each of these phases.
- Audit and Internal Control – Audits are a powerful tool for verifying controls are in place to prevent malicious individuals from penetrating security and obtaining control of systems and data. This includes assessing cyber risk and providing an objective assessment of cyber defense technologies and incident response plan completeness, coverage, and effectiveness. They are also useful in reviewing and auditing 3rd party vendors / partners / supply chains. Finally, auditors can provide valuable insight into control frameworks, standards, and best practices.
- IT/IS Asset and Change Management – Being able to track the location and configuration of networked devices and software is critical to reducing an organization's vulnerability to security threats. Otherwise, devices not on your radar may not be properly secured and may become the weak link by which threat actors gain access. Similarly, inadequate or inconsistent change management procedures leave the door open to unauthorized changes, which can lead to compromises of the confidentiality, integrity, and availability of data.
- Security Awareness Training – Security awareness training has always been a best practice, but it has become even more important in the current environment. Key components include: h1) how to recognize typical modes of attack, including social engineering; 2) customizing the training to address security needs of each work group; 3) requiring all personnel, including contractors, to regularly complete awareness training; and 4) covering best practices for securing the remote environment against cyber-attack.
- Risk Transference (Insurance) – In dealing with risk, organizations can select a risk treatment response (based on risk appetite) including acceptance, avoidance, reduction, sharing, or transference. When selecting insurance as a means of transferring risk, it should be noted that insurance policies are made up of declarations, insuring agreements, definitions, exclusions and conditions. Each of these sections need to be carefully reviewed as insurance companies are trending towards limiting their exposure by strictly interpreting policies to their advantage. Too often, organizations that believe they are covered are met with unpleasant surprises when their claims are denied after an event occurs.
Together, these five steps, together with the five provided in Part 1, will help your organization strengthen your security posture, keep a challenging situation from becoming disastrous, and withstand these attacks while keeping essential services running.
Stephen Head, CPA
Director, IT Risk Advisory Services
+1 704 953 6688
stephen.head@jeffersonwells.com
About the Author
Stephen has broad-based experience in cyber risk, regulatory compliance, IT governance and aligning controls with multiple standards and frameworks. He is the author of the internationally recognized Internal Auditing Manual and Practical IT Auditing, both published by Thomson Reuters, and has served as International Chair of ISACA's Standards Board. Stephen is a CPA, CISSP, CISM, CDPSE, CMA, CFE, CISA, CGEIT, CRISC, CBCP, MCSE, CHP, CHSS, CITP, CGMA, CPCU, and holds an MBA from Wake Forest University.
Software Supply Chain Cyber Attack: Part 1 and Part 2 should not be relied upon or construed as legal or financial advice. Organizations vary significantly in the risks they face, and these articles are no substitute for a thorough examination of your security ecosystem and risk posture. Please consult with your own Legal, Audit, Security, Compliance, and Finance resources before making any policy or procedure changes.
We welcome the opportunity to discuss your needs in this area and share our thought leadership to help your team. www.jeffersonwells.com






Comments